Posted by Zack Hamm on May 1, 2016

The Samsung SND-7084R is part of the WiseNetIII family of cameras from Samsung with 3 megapixel 1080p high definition images. It’s high level of functionalities includes 120dB Wide Dynamic Range which delivers 30fps at 3MP (60fps at 2 MP), low light performance down to 0.1 lux (F1.2, 50IRE, color) creating clear images in low light conditions, and has a built-in 2.8x motorized varifocal lens for easy focus control. The (R) designation in the model number is for IR illumination, allowing for 0 Lux B&W viewing. The unit is designed primarily for ceiling mounts, but a variety of mounting options are available from the manufacturer for alternative mounting options. Average Retail Price: under $600.00.
Notable features: 3MP @ 30FPS, Motorized zoom (3 ~ 8.5mm, no motorized pan/tilt but can be adjusted manually), Micro SD/SDHC slot, True Day/Night vision, IR LEDs for 0 Lux operation, Bi-directional audio capability, analog video out, intelligent video analytics (Tampering, Virtual line, Enter/Exit, (Dis)Appear, Audio detection, Face detection with metadata), defog, vide stabilization, and IPV4/IPV6 network connectivity with SSL, 802.1X, and QOS and full SNMP support.
Upon unboxing, the camera looks very well built, and includes all the connectors, mounting screws, and torx bits to install and service the camera. The included documentation was sparse, but the full online document manual is on disk and also available online here. The installation hardware includes both an “L” shaped torx wrench and a torx bit for a drill for easier installation. The camera housing is aluminum metal, with a tough lexan material dome suitable for vandal resistant applications. The dimensions are Ø132.1 x 107.6mm (Ø5.2″ x 4.24″), weight is 575g (1.27Lbs). Electrical requirements are 24VAC/12VDC @ 10W or PoE (802.3af Class 3) @ 11W maximum. Operating temperature range is -10°C ~ +55°C (+14°F ~ +131°F) / Less than 90% RH.

The camera has some nice additions that aren’t found on competing models, such as a dedicated analog video output connector, a built in SD/SDHC slot for video storage, audio in/out, zoom/focus switches on camera, defog fan, and phoenix connectors for power connections.
The CAT5 connection includes power and connectivity lights, but the orientation inside the case makes it such that connectors with long strain reliefs may be hard to fit inside the case. In most cases the cable will be field terminated anyway, so it’s probably not a big problem. Waterproof grommets are included to ensure a water tight seal for exterior installations. If you elect to use the additional connectors, note that they have fairly long leads on them, so be sure to include additional room in your mounting configuration. Although for most installations, a single CAT-5E cable is all that should be needed. There is some indication in the Samsung documentation that audio is available via a built-in microphone, but we could not locate a microphone anywhere on the unit, and were unable to hear any audio without the addition of a discrete microphone added to the audio input. We did not test the talk-back audio output feature. The connector to the left of the CAT5 connector is a multi-feature connector which has the audio in/out and alarm in/out harness. The alarm input/outputs were not tested.




Setup
We connected the camera both with 12VDC power and a standard 100BaseT Ethernet connection, and also with a PoE Ethernet connection. The camera booted up and connected via DHCP quickly under both configurations. We used the MAC address to find the IP assigned, and connected to the camera using Firefox on a Windows 10 computer. Note that like most IP cameras, you will need to first download and install their specific codec in order to view any video. This necessary step is a hassle because it requires a browser restart, but it only needs to be done once.
When first connecting to configure, you must set a password… a really, long, complex password. For testing, I just set it to “Admin1223!”. Username default is “admin”. The setup configuration menus are intuitive and fairly common among other IP cameras, and the menus were very responsive and quick to acknowledge configuration changes. We first connected to verify we had video, and then began looking at default configuration settings and features. Since nobody likes upgrading firmware, we pleasantly noted this unit shipped with the latest version of firmware, which as of this writing is 3.00_140915. Notable features on the configuration defaults are that SNMP V2 is on by default with public read/write, DHCP is enabled by default (this is a good thing), and UPnP and Bonjour discovery services are enabled by default (this is not a good thing).
Date/Time – The camera also supports timezones and NTP time synchronization, with support for up to 5 NTP servers (why, we’re not sure, but okay). TCP ports are also fully configurable for HTTP, HTTPS, RTSP, and the Device Port. IPV6 is disabled by default.
Users – Multiple users are supported, and we recommend setting up an NVR user/password and then making the default admin password really complex (it should already be anyway). It does not appear possible to rename the admin user or delete it. You can also have RTSP connections without authentication, but we would not recommend it.
Events – The events tab configures how the camera senses activity/events and responds to them. Notable features are face detection (which worked rather well), and motion detection/video analytics which also worked well and was easy to configure. However, the event triggers seemed to be limited to the camera only, meaning you could trip an alarm output (DO), record to SD/SDHC, or send video via email or FTP. There did not appear to be any methods to send logical alarm event outputs to the NVR or VMS, leaving most of these features best residing on the head end software platform for most applications. We should also note however, that while we are aware an SDK from Samsung that would likely allow for passing logical video alarm events exists, we also have not asked the manufacturer for relevant information about it and have not verified integration with other NVR manufacturers about compatibility. We also noted that NAS support is available, and alarm events can trigger automatic recording to the NAS device, although this feature was not tested.
Camera Setup – Multiple profiles are supported, with backlight compensation, WDR, AWB, and day/night modes all worked well in our testing under different lighting conditions. We were unable to find a way to export/import camera profile settings however, and feel that for an enterprise installation, a shared profile among cameras that could be imported during installation would make installations easier and more uniform.
Focus Setup – Focus/Zoom was configurable by a joystick switch on the camera body itself, and via software in the configuration menu. It was less than intuitive however, and the “Simple Focus” feature really didn’t seem to help set a specific field of view as we’d hoped. For a varifocal camera, we expected to be able to set the view and autofocus would take care of itself. We also were unable to remotely zoom via our NVR software, even though it detected OXML PTZ control via ONVIF.
Setup for NVRs
Note the URL for RTSP viewing from your NVR, if not automatically configured via ONVIF, would be “/profile2/media.smp”. At least that’s what worked in our testing. Our VMS software did not correctly identify the ONVIF RTSP URL, and we had to input the string manually. The correct URL was not documented in the setup instructions as best we could determine.
Also on the camera setup page under “Video Profile”, the ‘profile’ setting may need to be changed from “High” to “Baseline” for some NVRs, in order to work properly. Other settings, FPS, resolution, codec, bitrate, etc. should be changed as suitable.
Summary
Overall the build quality and features of the Samsung SND-7084R are very good. We found most of the built in software features easy to use and effective, and image quality and stability was excellent. Warranty for the camera is 3 years. We feel this camera is suitable for commercial and government installations, and depending upon the video management system, could be suitable for enterprise installations that could take advantage of it’s embedded video analytics.

Tags: IP Cameras, NVR
Posted in: Reviews

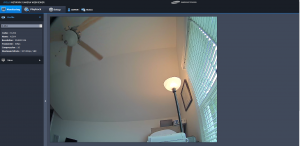
 The objective was to have a decorative camera that would recognize video motion and record video and sound for visitors at the doorstep.
The objective was to have a decorative camera that would recognize video motion and record video and sound for visitors at the doorstep.

 accounts have been affected in one of the largest data breaches in history. My Yahoo account was one of them, although I only used it as a personal dump account for registering on non-essential websites. Luckily I kept no personal or financial information in any of the emails there.
accounts have been affected in one of the largest data breaches in history. My Yahoo account was one of them, although I only used it as a personal dump account for registering on non-essential websites. Luckily I kept no personal or financial information in any of the emails there. old, yellow street lights now shine bright white and bright with the latest in modern street lights, LEDs. LED lights are popular because of their tremendous energy savings, about 80-90% energy efficiency, when compared to a traditional incandescent light bulb. This means the LED lamp has about 80% of the energy used to illuminate actually goes into making the light, with the remaining 20% given off as thermal energy. Compared with the highly inefficient incandescent bulb, which is about 25% converted to light, and 75% given off as heat. So for any business, residence, or municipality, a huge savings in operating costs can be found by switching to LED lighting, and with federal subsidies for energy savings, the capital costs are partially offset as well.
old, yellow street lights now shine bright white and bright with the latest in modern street lights, LEDs. LED lights are popular because of their tremendous energy savings, about 80-90% energy efficiency, when compared to a traditional incandescent light bulb. This means the LED lamp has about 80% of the energy used to illuminate actually goes into making the light, with the remaining 20% given off as thermal energy. Compared with the highly inefficient incandescent bulb, which is about 25% converted to light, and 75% given off as heat. So for any business, residence, or municipality, a huge savings in operating costs can be found by switching to LED lighting, and with federal subsidies for energy savings, the capital costs are partially offset as well.









