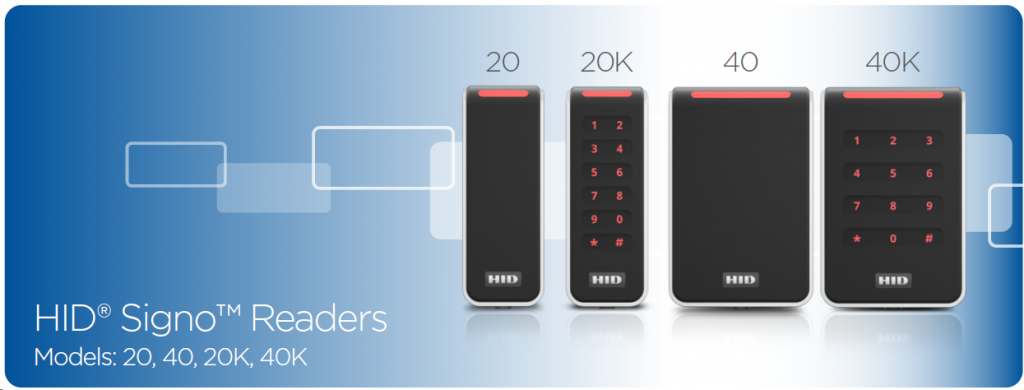
HID Signo Readers Announced.
HID announced an entirely new reader line today, called Signo. What’s immediately noticeable is they are more sleek and stylish than the iClass R or RP models, but looking further, we found that there are some distinct differences that might just make switching to this new reader platform sensible.
For starters, the keypad reader model looks more functional, and the mullion keypad reader is a definite necessity. The keypads are capacitive touch style which should make them more reliable in harsh environments.
Dimensions for the readers is almost identical, with the Signo readers being a little slimmer, but probably not by very much. See Feature Comparison Matrix.
What’s missing though, like in the RP series, is a long range parking lot reader like the R90. This is a needed technology that should be added in the future (are you listening, HID?).
The Signo series seems to lump all the reader technologies in together, making the product selection a little less confusing than previous iClass reader selections. This is most welcomed. Supported technologies are 125Khz proximity, iClass, SEOS, Mifare, plus mobile credentials via Bluetooth and NFC, plus Apple’s Enhanced Contactless Polling technology for apple wallet credentials.
Other features are better support for crypto keys (no more base encryption key in the wild, for now), automatic tuning/detuning for optimized read range, and OSDP support out of the box. Reader tamper is now a dry contact relay (THANK YOU). But the biggest thing installers are going to enjoy is that the Signo readers support remote management. No more configuration cards to go around to every reader just to turn of the 125Khz prox read feature set. This should have been done LONG AGO. Firmware updates, configuration, and reader management can be done via mobile device or over OSDP (assuming your PACS supports it).
From our take, these readers appear to have been developed largely for the Campus environment (the Apple ECP is a dead giveaway), but certainly have the feature sets that would make them desirable in the commercial, government, and industrial markets as well. We don’t have any evaluation copies yet, but will definitely be looking at these for new projects where they fit and offer additional security, style, and convenience.
Feature Comparison Matrix
| Reader | RP40 | Signo 40 |
| Dimensions | 3.3″ x 4.8″ x 1.0″ | 3.15″ x 4.78″ x 0.77″ |
| Read Range (typ) |
iCLASS: 2.4″ 125Khz Prox: 2.8″ to 4.3″ |
iCLASS: 1.6″ to 4″ 125Khz Prox: 2.4″ to 4″ |
| Power | 85ma @ 16VDC | 75ma @ 12VDC |
| Comm | Wiegand & (optional) OSDP | Wiegand & OSDP |
| Reader Tamper | Open Collector Output | Dry Contact Relay |
| Configuration | Programming Cards | Mobile Device or OSDP |
| Weatherproof | If optional gasket installed | Yes |
| Certifications | UL294, EAL5+ | UL294, EAL6+ |
| Price | ~$200.00 | ~$200.00 |