Hacking Sony – Corporate culture broken from the top down
One of the questions I keep asking myself as I keep reading the dozens of recent articles about how Sony got hacked by “North Korea” is, why does 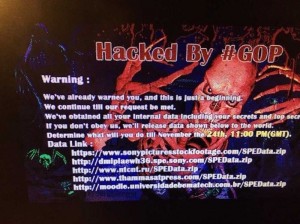 Sony KEEP getting hacked?
Sony KEEP getting hacked?
The short answer is “because they can”. But the longer answer points to a corporate culture that doesn’t understand the need for protection of information assets, or the people who are constantly after those assets.
On November 24, Sony discovered that its corporate network had been hacked. The attackers took terabytes of data, deleted the original copies from Sony computers, and left messages threatening to release the information if Sony didn’t comply with the attackers’ demands. But it was really much worse, not only was work disrupted as Sony’s IT professionals scrambled to recover lost data and restore data services, much of the proprietary information of Sony Corp. was released into the public domain for everyone to see. Unreleased movies, private email conversations, celebrity contact information, social security numbers, passwords, and salary information were released into the wild. The damage will be felt for years to come.
I’m uncertain of the actual number of cyber attacks on Sony (and only Sony knows the real number), but this latest attack has to put it somewhere in the high teens. This attack was the latest of a string of attacks that has been happening since 2003, mostly related to Sony’s DRM policies and certain lawsuits over “hacking” the Sony PS3 platform. At least, that’s where I think it all began. Since then, it’s become the “hip” thing to do for black hats, Hack Sony. The notion that North Korea is behind this latest attack as claimed seems pretty thin to us, and also to the FBI in their official statements so far.
But what really is the cause of this? From what I have read, it looks like it stems from a top down culture of a lack of respect for information security. Their IT security department is woefully thin, understaffed for a company of Sony’s stature, security equipment and software was not properly installed, policies not enforced, and even simple things like compartmentalization of data, like keeping performer contracts or salary information separate from other data sources, were apparently not properly implemented. This seems odd, since much of the technology Sony has developed (or bought) for DRM and copyright protection is fairly sophisticated, and expensive to develop.
Skipping the technical aspects of what Sony should have done or should now do to protect itself from cyber security, I will just propose in simple layman’s terms what a company in Sony’s position should consider across their corporate footprint.
- A top down philosophy of information security starting with corporate officers.
- Increased IT security staff and technology solutions to better identify, insulate and protect from cyber threats.
- Corporate wide training in information security, compartmentalization, best practices for data security and user authentication.
- Mandatory periodic password audits for all personnel (no Prima donnas who can’t remember a password).
- Two step authentication for most or all access, especially to sensitive information repositories.
- Regular security audits for physical and IT security.
- Personnel background checks, exit interviews with binding nondisclosure agreements.
- Active content filtering for incoming and outgoing internet traffic, strict VPN use for remote sites, and GEO IP security filtering at the desktop level.
- Active enforcement of corporate policies and legal prosecution for data breach events by employees or contractors.
Meanwhile, the media will be poring over mountains of sensitive information they shouldn’t have, hoping to find the next juicy bit of “Sony Dirt” to release in it’s next news cycle.
